
(Image source from: Mark Zuckerberg's Facebook account hacked})
Last week, security researcher from Palestine, Khalil Shreateh spotted a Facebook bug that would let a hacker post on anyone’s wall — even if he/she weren't on his/her friends list.
When Facebook refuted his claims, he hacked into Mark Zuckerberg's Facebook Wall to prove that the bug was legit. Needless to say, Facebook wasn't too happy with the way he did it.
In his initial report, Khalil explained how he could post on anyone’s wall by submitting a link to a post he’d made on the wall of Sarah Goodin (a college friend of Zuck’s, and the first woman on Facebook.)
Unfortunately, the member of the Facebook Security team who clicked the link wasn’t friends with Goodin, whose wall was set to be visible to friends only. As a result, they couldn’t see Khalil’s post.
“I don’t see anything when I click the link except an error”, responded Facebook’s Security team.
Khalil submitted the bug with the same link again, explaining that anyone investigating the link would need to either be Goodin’s friend or would need to “use [their] own authority” to view the private post.
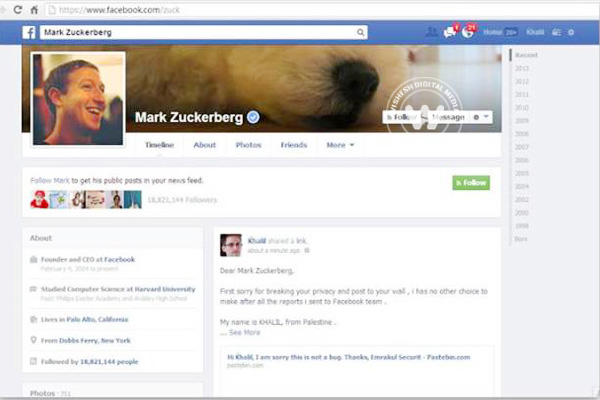
“I am sorry this is not a bug”, replied the same member of the Security team, seemingly failing to grasp what was going on.
Khalil responded by taking his demonstration to the next level; if posting on one of Mark Zuckerberg’s friend’s walls didn’t get his point across, perhaps posting on Zuck’s own wall would?
On Thursday afternoon, Khalil posted a note into Zuckerberg’s timeline. “Sorry for breaking your privacy [to post] to your wall,” it read, “i [had] no other choice to make after all the reports I sent to Facebook team”.
Within minutes, Facebook engineers were reaching out to Khalil. He’d made his point.
As per Facebook’s whitehat exploit disclosure program, security researchers are awarded $500 for each critical bug they report responsibly. $500 is the least — the size of the bounty goes up with the severity of the bug, with no set maximum.
Sadly, there would be no bug bounty for Khalil! Ask why? Well, Facebook’s bug disclosure policy terms clearly states that the researcher reporting a bug should use test accounts for their investigations and reports, and not accounts of other Facebook users. By posting to Goodin and Zuck’s walls, he’d pretty much broken those policies. Besides, his reports didn’t offer adequate detail of how to reproduce the bug, says Facebook:
“Unfortunately your report to our Whitehat system did not have enough technical information for us to take action on it. We cannot respond to reports which do not contain enough detail to allow us to reproduce an issue. When you submit reports in the future, we ask you to please include enough detail to repeat your actions.We are unfortunately not able to pay you for this vulnerability because your actions violated our Terms of Service. We do hope, however, that you continue to work with us to find vulnerabilities in the site,” said Facebook.
Since Khalil’s initial post went up on Friday, there’s been a strong debate as to whether or not Facebook should give him hi bounty. On one hand, he violated their disclosure rules (perhaps unknowingly — as many have pointed out, Facebook’s disclosure terms are only available in English, which doesn’t seem to be Khalil’s first language); on the other, he was seemingly trying to report it responsibly rather than selling it to spammers.
What's your take on it? Should Facebook bend the rules and pay Khalil his bounty?
News Source: AOL
AW: Suchorita Dutta




















